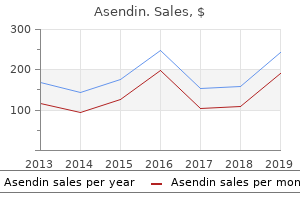
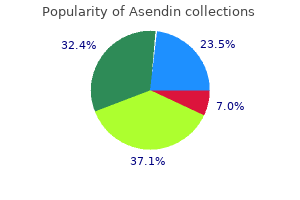
"50 mg asendin sale, bipolar depression evaluation".
By: Q. Jack, MD
Assistant Professor, Northwestern University Feinberg School of Medicine
In particular definability over the natural number structure later became extended to considering the notion of hyperarithmetic definability: sets of numbers that whilst not recursive depression response definition order 50 mg asendin visa, or even obtainable by finitely many iterations of the Turing jump operator anxiety 7 year old son purchase asendin without prescription. Such notions then connect to the theory of inductive definitions over N as now described depression urban dictionary order genuine asendin online. The other direction initiated by Kleene mood disorder treatment plan buy asendin 50 mg otc, who published his equational system of recursion in higher type objects in a series of papers from 1959 onwards. He himself devised a notion that came to be called Kleene Recursion: this was a higher type recursion with a domain that of all the real numbers, that allowed hyperarithmetic questions about membership of sets of such numbers to be answered. However the science of higher type recursion theory later became much developed by the work of Gandy, Moschovakis, Harrington, Normann, Kechris, et al. Indeed it did, but these formulations, and indeed much of the generalised theory of inductive definitions, and the later theory of Spector classes of Moschovakis became intimately involved with the notion of admissible set. A transitive set M was an admissible set if it was a model of some modest basic set theory, including schemes of 1 -Comprehension and 1 -Replacement. In particular those levels of (relativised) Godel hierarchies of the form L [A], A that were admissible came to play Ё a central role. The importance of admissible sets was that they 112 Part I were domains inside which certain natural 1 -set theoretic recursions or constructions (rather than number theoretic) could be effected. Much of this may seem a million miles from the original conceptions of recursive set of integers and universality of the computation/recursion procedure that allowed for the Enumeration and Recursion Theorems etc. However these founding theorems return, almost partly as definitions, in the notion that Moschovakis singled out as encompassing a generalised theory of inductive definability, that of the Spector class. We give the definition (with some details swept under the rug) as it pertains to inductive definitions at the lowest type, those of sets of integers. The last property here is somewhat distractingly technical, and so has been left vague, but the point is that the function into the ordinals, gives us a nice prewellordering of the set P and in a very loose sense, we can think of it as saying that an n gets into P before m does if (n) < (m). Property (ii) is recognisable as an Enumeration property; (i) hints at some initial basic closure properties. There are countless examples of Spector classes, but the original basic such ur-class is obtained by taking the class of 1 sets of integers (and this is the least such class). Such classes relate to 1 notions of definability over admissible sets, since to any Spector class of sets of integers we may find an admissible structure M over which the sets in correspond to sets inductively definable over M via some operator as above. So, on the one hand, the increasing generalisations of recursion theory to higher types, and especially those including infinite ordinals in their domain, were mostly mathematical generalisations rather than machine model generalisations. This might lead one to think that with the increasing sophistication of the approach, that the original intuition of machine or computer had been left far, far behind. However running through this development was always a thread of machine-mindedness. In short anything that a mind capable of comprehending, and acting on, an 0 =sized amount of information could do. In a realistic sense (pace the countably infinite processes involved) this can still be construed as a machine model. Toward the Unknown Region: On Computing Infinite Numbers 113 the recent two decades however has seen an expansion of interest in generalising models of computation, and this has led to mathematical investigations of models of computation where one or more space or time parameters are relaxed: the model of the Infinite Time Turing Machine of Hamkins and Lewis (2000) allows time to become transfinite. One simply has to specify a behaviour at limit stages of time: thinking of the ordinary Turing machine model, as the program is finite, if the machine does not halt but runs for an -sequence of steps, then it is in a program loop; so at time put it at the beginning of the outermost loop or subroutine in which it was involved (in other words at the least instruction number it visited infinitely often below). Hamkins and Lewis (2000) does this differently, by having three tapes, a 0/1 alphabet only and by taking limsups at limit ordinals, and placing the head back to cell C0 at all limit times. We can devise oracle machines that, like Kleene Recursion, can quiz a set of reals. Consider another machine: if we are relaxing time, why not go the whole hog and relax space considerations too? In short, followЁ ing such considerations, we have another presentation, now a machine theoretic presentation, of the set-theoretic Godel L-hierarchy to set aside those alternatives of Jensen (1972) and Deutsch (1985) Ё Sec. We may have ordinary Turing style-action at successor stages, but the limit rule is a kind of infinitary logical rule integrating over this time dimension. It may look innocuous to put B-blanks on tapes at infinite stages, or take a liminf of previous cell values, but it is in these actions that the whole essence of the process inheres. We now define for such a (no longer required to be monotone): 0 (X) = X; (X) = lim inf +1 (X) = (X) =df ((X)); (X) < >> for limit. Such do not necessarily reach a fixed point but instead (after countably many iterations) reach a stability point: a least stage = (X) so that (X) periodically returns for ever after as runs through all the ordinals. Starting with the natural numbers the quasi-inductive sets defined by arithmetic (or hyperarithmetic) operators again form a natural Spector class.
In fact anxiety no more buy asendin 50 mg cheap, some might even be surprised to learn that his early work was this explicitly dedicated to such anxiety pills buy asendin 50 mg without a prescription. It would seem to be its patently practical nature and its mechanical commitments that challenge our picture of a mathematical Turing by presenting another Turing depression checklist generic 50mg asendin visa, the mechanist anxiety 35 weeks pregnant buy discount asendin online, who gets into the nuts and bolts of computing machinery. In doing so, as I have tried to make clear, he does not show a clean break that starts a new era, but strong attachments to the preceding one. This is not to suggest that Turing did not issue in an unprecedented era in the processing and storage of information and the speed of its dissemination. In this regard, I wish to close with one final comment about technological visionaries in general. Turing foresaw the possibility of connecting the computer to the telephone in much the same way that Edison did. Then, when a person wants to telegraph to a friend, he knows not where, he will call in an electro-magnetic voice, which will be heard loud by him who has the electro-magnetic ear, but will be silent to everyone else. No one back then, it seems, could imagine what would happen when the computer revolution, inaugurated by Turing, and the telephone revolution, inaugurated by Bell, would come crashing together at the end of the twentieth century to connect everyone to computers (both human and mechanical) by way of hand-held computer/telephones and other devices that are both affordable and have more computational power than Turing himself imagined practical. We stand on the shoulders of giants, information visionaries of the past 200 years. This makes it all the more shameful that Turing himself was never permitted to experience the appreciation of a world that owes him an incredible debt, not solely because of his brilliant mind, but also because he was not afraid to get his hands dirty. We should never disparage those who are willing to get dirty in the process of making the world a better place. In the beginning was the word and then four revolutions in the history of information. A History of Wireless Telegraphy, 18281899, Including Some Bare-Wire Proposals for Subaqueous Telegraphs, William Blackwood and Sons, London. Vision: A Computational Investigation into the Human Representation and Processing of Visual Information, W. In a single lecture it will not be possible to give much technical detail of this machine, and most of what I shall say will apply equally to any other machine of this type now being planned. From the point of view of the mathematician the property of being digital should be of greater interest than that of being electronic. That it is electronic is certainly important because these machines owe their high speed to this, and without the speed it is doubtful if financial support for their construction would be forthcoming. It means firstly that numbers are represented by sequences of digits which can be as long as one wishes. This accuracy is not obtained by more careful machining of parts, control of temperature variations, and such means, but by a slight increase in the amount of equipment in the machine. To double the number of significant figures used would involve increasing the equipment by a factor definitely less than two, and would also have some effect in increasing the time taken over each job. This is in sharp contrast with analogue machines, and continuous variable machines such as the differential analyser, where each additional decimal digit required necessitates a complete redesign of the machine, and an increase in the cost by perhaps as much as a factor of 10. A second advantage of digital computing machines is that they are not restricted in their applications to any particular type of problem. The differential analyser is by far the most general type of analogue machine yet produced, but even it is comparatively limited in its scope. It can be made to deal with almost any kind of ordinary differential equation, but it is hardly able to deal with partial differential equations at all, and certainly cannot manage large numbers of linear simultaneous equations, or the zeros of polynomials. With digital machines however it is almost literally true that they are able to tackle any computing problem. Some years ago I was researching on what might now be described as an investigation of the theoretical possibilities and limitations of digital computing machines. I considered a type of machine which had a central mechanism, and an infinite memory which was contained on an infinite tape. It was essential in these theoretical arguments that the memory should be infinite. It can easily be shown that otherwise the machine can only execute periodic operations. Digital computing machines all have a central mechanism or control and some very extensive form of memory.
Generic asendin 50mg amex. You Won't Believe- A Natural Substitute for Xanax?!? How Does NOBODY Know About This?!.
This is useful to the target workstation and saves it from having to initiate a neighbor discovery process of its own when it sends a packet back to the source workstation depression definition nach who generic asendin 50mg on-line. When this bit is set on depression or anxiety quiz 50 mg asendin with visa, the receiving node must update an existing cached link layer entry in its neighbor cache depression test beyond blue purchase asendin without a prescription. After workstation A receives this packet mood disorder 6 year old buy generic asendin line, it commits the information to memory in its neighbor cache, and then forwards the data packet that it originally wanted to send to workstation C. Neighbor advertisement messages can also be sent by a node to force updates to neighbor caches if it becomes aware that its link layer address has changed. In a larger network, particularly one connected to the Internet, the neighbor discovery process is used to find nodes on the same link in exactly the same way. However, it is more than likely that a node will need to communicate not just with other nodes on the same link but with nodes on other network segments that might be anywhere in the world. The format of the router advertisement message is shown in Figure 9-18 on page 358. The message generally has one or more attached options; this example shows all three possible options. If this time period is exceeded and the node has not received another router advertisement message, the node should consider this router to be unavailable. It is the time in milliseconds that the node should assume a neighbor is still reachable after having received a response to a neighbor solicitation. This sets the time, in milliseconds, that nodes should allow between retransmitting neighbor solicitation messages if no initial response is received. For some media, such as Ethernet, this value is fixed, so this option is not necessary. Nodes use this information to determine when they do, and do not, need to use a router. Prefix options are also used as part of address configuration, in which case the A bit is set on. Option 3 (Prefix) A router constantly sends unsolicited advertisements at a frequency defined in the router configuration. A node might, however, want to obtain information about the nearest router without having to wait for the next scheduled advertisement Chapter 9. Destination address this address is the special multicast address defining all routers on the local link. Option 1 (source link address) Allows the receiving router to respond directly to the node without having to do a neighbor solicitation. Redirection the router advertisement mechanism ensures that a node will always be aware of one or more routers through which it is able to connect to devices outside of its local links. However, in a situation where a node is aware of more than one router, it is likely that the default router selected when sending data will not always be the most suitable router to select for every packet. Node Y Router B Router A Node X Figure 9-20 Redirection example Consider the simple example shown in Figure 9-20. Node X is aware of routers A and B, having received router advertisement messages from both. A node actively tracks the reachability state of the neighbors to which it is sending packets. When a path to a neighbor appears to be failing, appropriate action is taken to try and recover the link. This includes restarting the address resolution process or deleting a neighbor cache entry so that a new router can be tried in order to find a working path to the target. The node attempts to verify that this tentative address is unique by issuing a neighbor solicitation message with the tentative address as the target. If the address is already in use, the node will receive a neighbor advertisement in response, in which case the autoconfiguration process stops. If no response is received, the node assigns the link-level address to its interface. The host then sends one or more router solicitations to the all-routers multicast group. If a router advertisement is received in response to the router solicitation, this message contains several pieces of information that tells the node how to proceed with the autoconfiguration process (see Figure 9-18 on page 358): M flag: Managed address configuration. If the information in the advertisement changes, the node must take appropriate action. Note that it is possible to use both stateless and stateful configuration simultaneously.
An appropriate hypothesis for the purpose is the following: the third principal parastichy number does not lie numerically between the first and second depression gad symptoms cheap asendin 50 mg without a prescription. The longest side should either join the uppermost and lowermost points of the triangle emotional depression definition buy generic asendin 50mg on line, or else be sufficiently nearly horizontal for its projection onto a vertical line to be less than half the projection of the whole triangle anxiety attack vs panic attack asendin 50 mg online. If this be not so then there must be a time when the principal parastichy numbers change from a set pr-1 depression test india discount asendin 50 mg on-line, pr, pr+1 obeying the rule to a set which do not. This must arise through the original third parastichy number being dropped out and being replaced by another number. It cannot be pr-1 which is dropped, for then pr, pr+1 would remain, and by §4 the third parastichy number after the change must be either pr+1 - pr or pr+1 + pr, i. It cannot be pr for the Morphogen Theory of Phyllotaxis 791 this would contradict the hypothesis of geometrical phyllotaxis. Thus each alternative is impossible, and the assumption that it is possible to reach principal parastichy numbers not in the series pr is contradicted. However true it is, and however logically it follows that the principal parastichy numbers remain in a Fibonacci-like series, the hypothesis is itself quite arbitrary and unexplained. Its merit is that it replaces an empirical law, of a rather weird and magical appearance, by something simpler and much less mysterious. There are other questions which it is also unable to answer, such as "Why should leaf patterns take the form of lattices at all? There remain however a number of questions which can be treated by the methods of geometrical phyllotaxis, which have not yet been considered. The inverse lattice Suppose that one does not consider the leaves as geometrical points but as described by some function on the surface of a cylinder, or in the plane obtained by unrolling the surface of the cylinder. The points of the cylinder may be expressed in the form (1, 2) since the matrix a c b d a c b = (x, z) d is non-singular. When the function is described in terms of the variables (1, 2) it is periodic with unit period in both variables, i. To express this in terms of the original variables one must express (1, 2) in terms of (x, z). If the A C a b inverse of c d is B D then 1 = Ax + Bz, and the function can be written as Am,n e2i((mA+nC)x+(mB+nD)z) or as f (x) = Au e2i(u,x) (I. This lattice may be called the inverse lattice, because it is described by the transposed inverse of the matrix describing the lattice arising from the congruences. In the inverse lattice it is only the lattice points relatively close to the origin that are of any particular importance. Consider for example a function in the plane having the symmetry of the a b lattice, and of the form yL g(x + y) where L is the lattice c d. If mJ and nJ are two parastichy numbers, if the corresponding vectors generate the lattice, and if the parastichies make angles 1, 2 with the generators of the cylinder, then the matrix J 2 n n2 -m -m1 is one of the matrix descriptions of the inverse lattice. In other words, the first coordinates of the points of the inverse lattice are all multiples of J/2. This simply represents the fact that the leaf pattern is unaltered by rotating the cylinder through the angle 2/J. When drawing diagrams to describe a phyllotaxis through its inverse lattice, it is helpful to draw a number of vertical lines, u = m/2 or possibly only the lines u = mJ/2. The points of the inverse lattice are bound to lie on these lines, and may be imagined as beads sliding up and down on them. Owing to the fact that only relatively few points of the inverse lattice can be of importance it is appropriate to use a relatively large scale for such diagrams, i. It may be noticed that, apart from scale, the two lattices are obtainable from one another by rotating through 90; the scale factor is or -1. To a large extent, however, it will no longer be possible to work in terms of lattices. To assume that one has a lattice is an approximation which is no longer appropriate when discussing the origin of the phyllotactic patterns. It is nevertheless still appropriate to describe functions on the surface of the cylinder by a Fourier analysis of some kind. The appropriate kind of Fourier analysis for functions defined on a cylinder is of the form of a Fourier series in one variable and a Fourier integral in the other: f (x, y) = m=- - Fm (v)e(imx/P)+ivy dy.